
Authenticate This LV: READ the rules & use the format in post #1, Page 588

Authenticate This LV: read the rules & use the format in post 1, Page 112
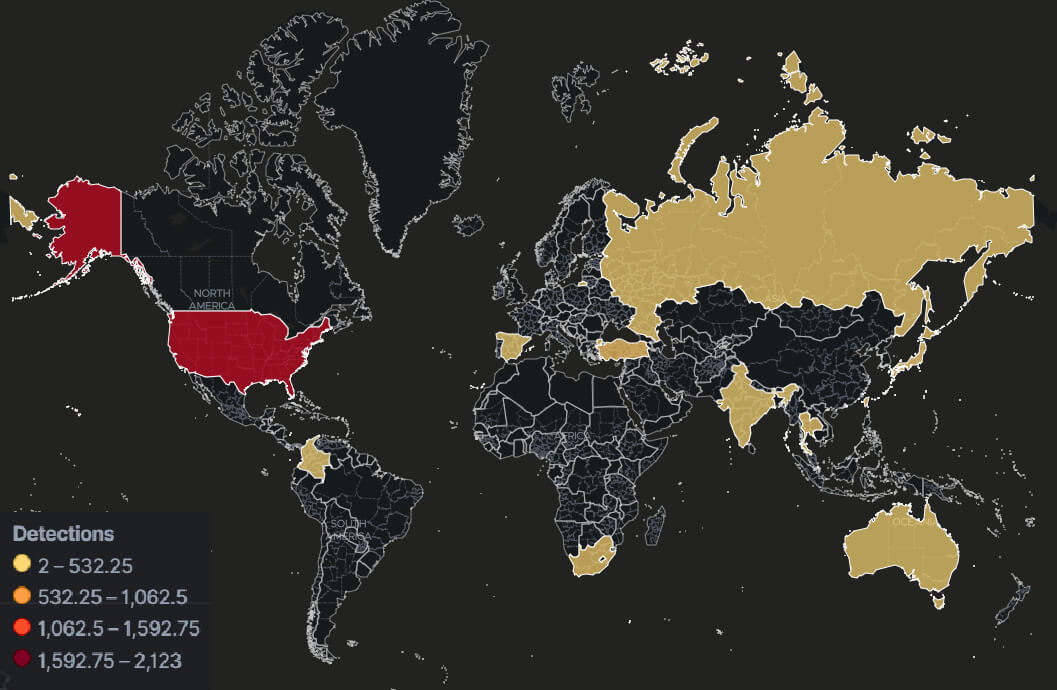
Global ESXiArgs ransomware attack on the back of a two-year- - vulnerability database

Authenticate This LOUIS VUITTON - Read 1st Post BEFORE POSTING!
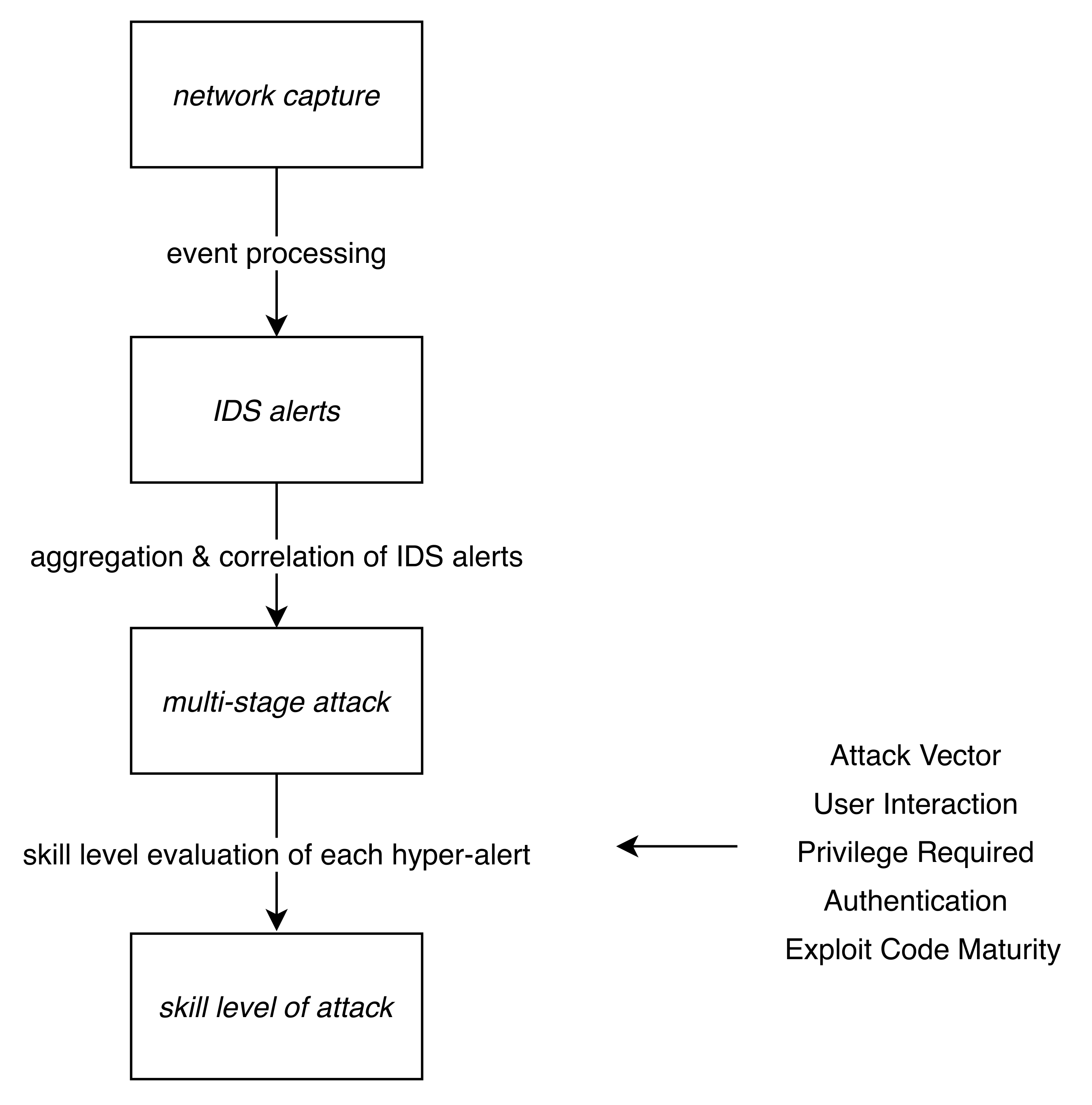
Information, Free Full-Text
PDF) Intelligent authentication, authorization, and administration (I3A)
Mass Override Service Variables in Director - Icinga Director - Icinga Community

Against the Grain v31 #3 June 2019 by against-the-grain - Issuu
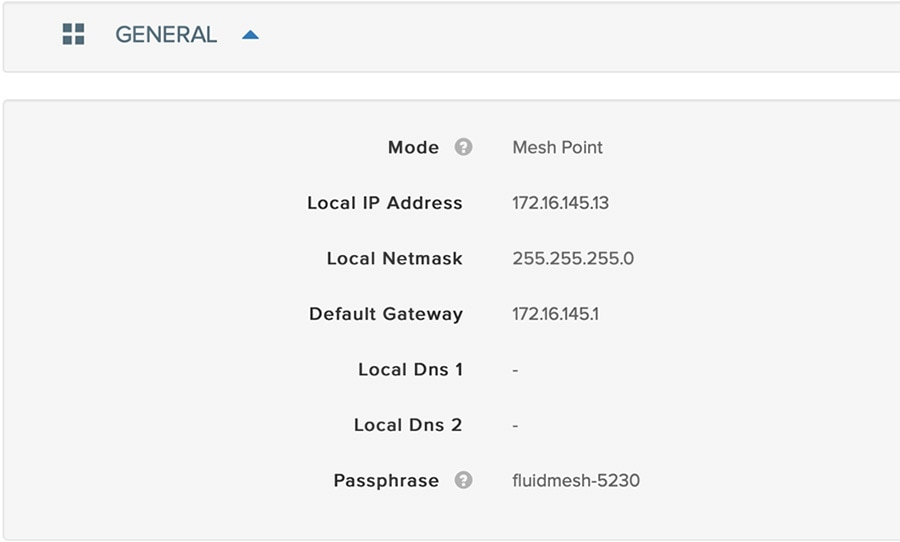
Connected Communities Infrastructure Solution Implementation Guide - Connected Communities Infrastructure Solution Implementation Guide [Solutions] - Cisco

Authenticate This LOUIS VUITTON - Read 1st Post BEFORE POSTING!
