
Client to Authenticator Protocol (CTAP)
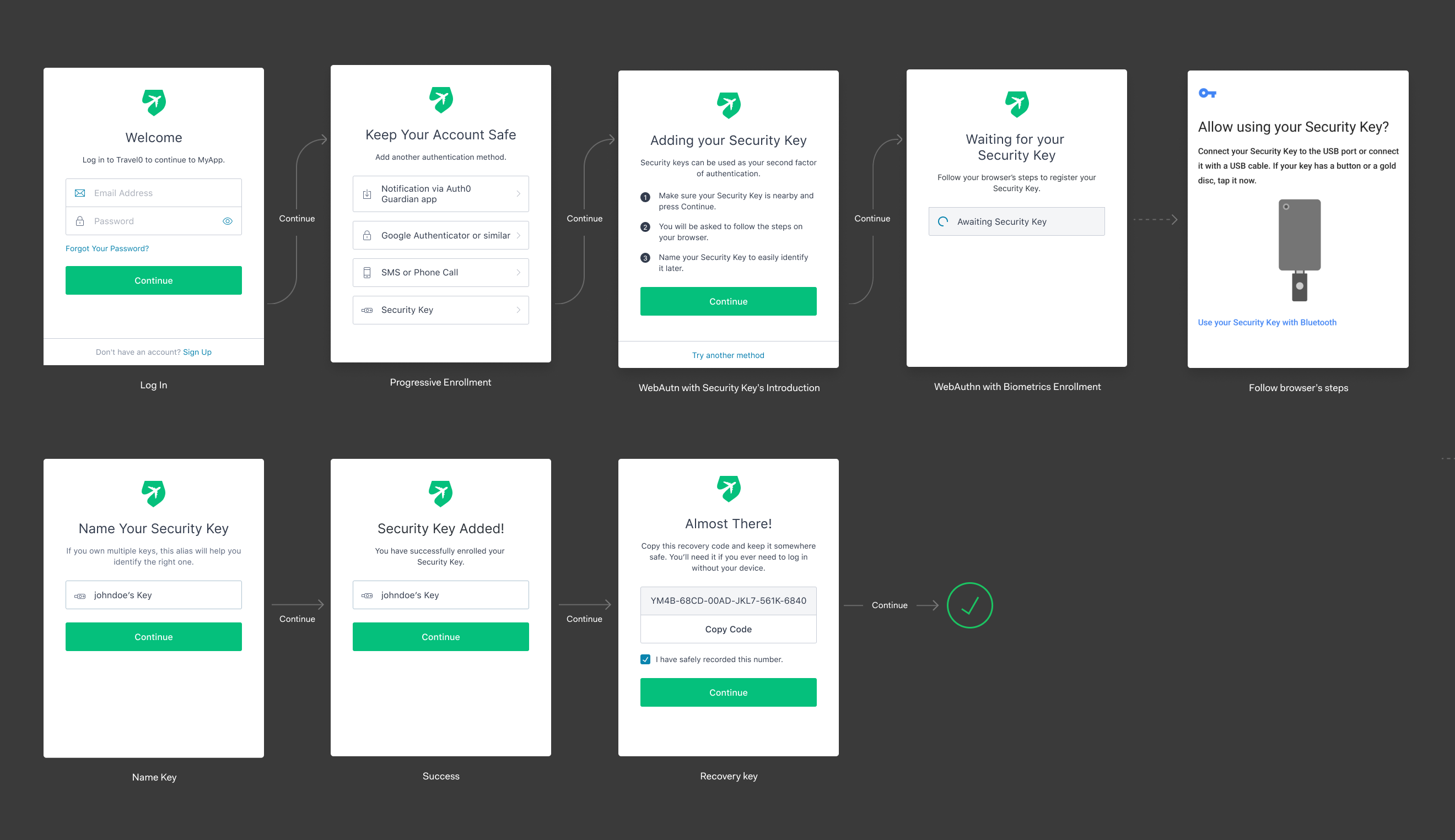
FIDO Authentication with WebAuthn
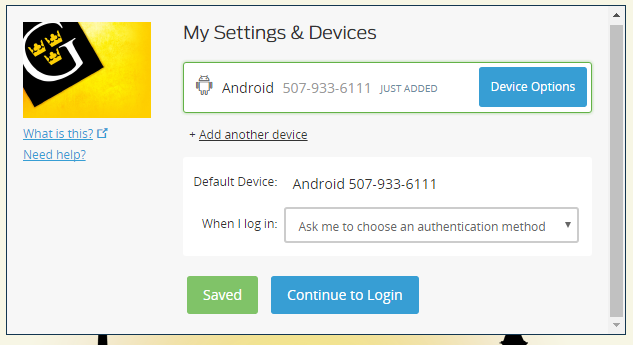
Duo Two Factor Authentication

Token2, Token2 T2F2-PIN+/TypeC FIDO2, U2F and TOTP Security Key with PIN complexity feature, TOKEN2 MFA Products and Services
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey
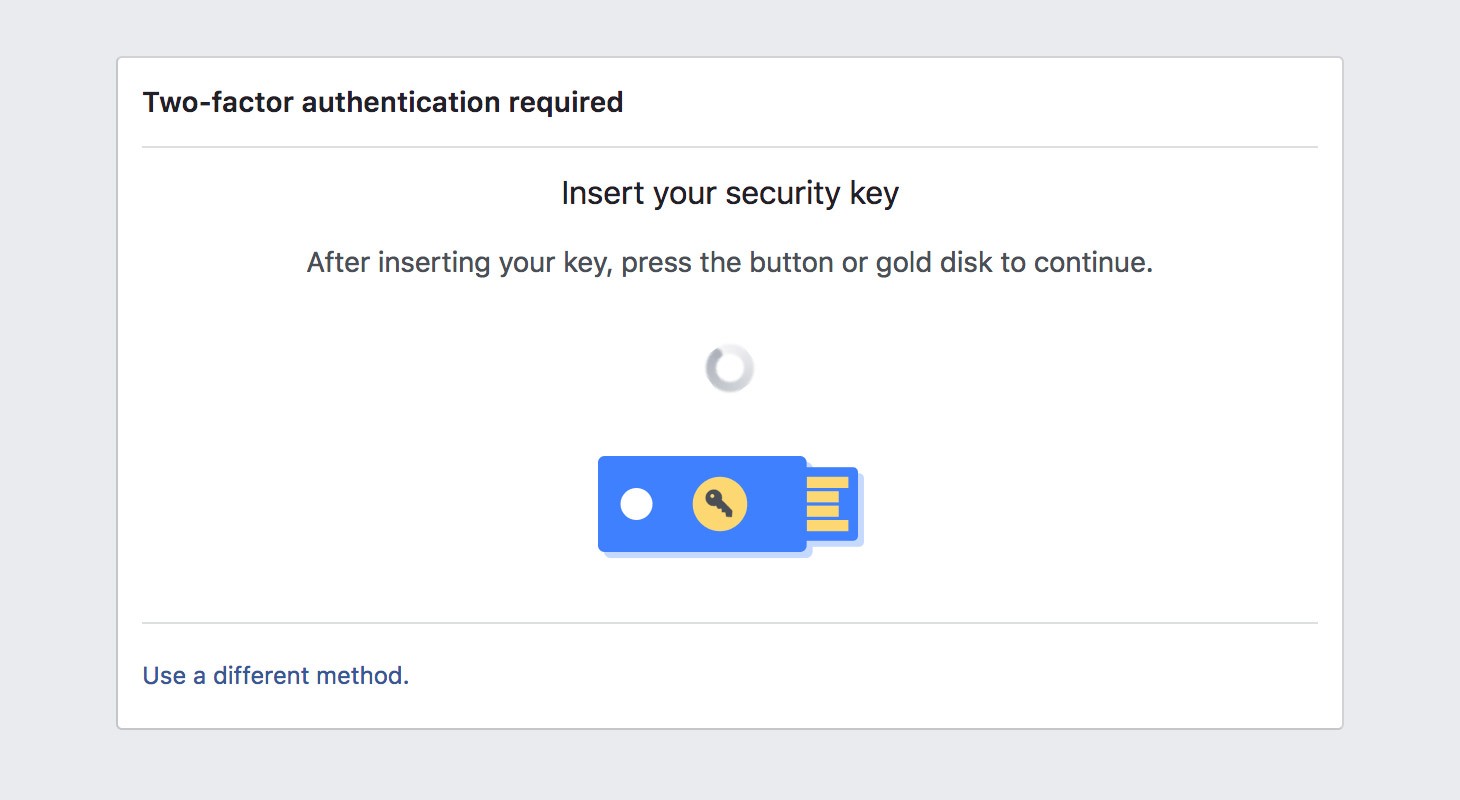
Types of two-factor authentication, pros and cons: SMS, authenticator apps, YubiKey

How to set up 2-Factor Authentication (2FA) - UW Finance - Technology Shared Services - UW-IT Wiki

Windows, Linux Devices Hijacked In Two-Year Cryptojacking Ca - vulnerability database
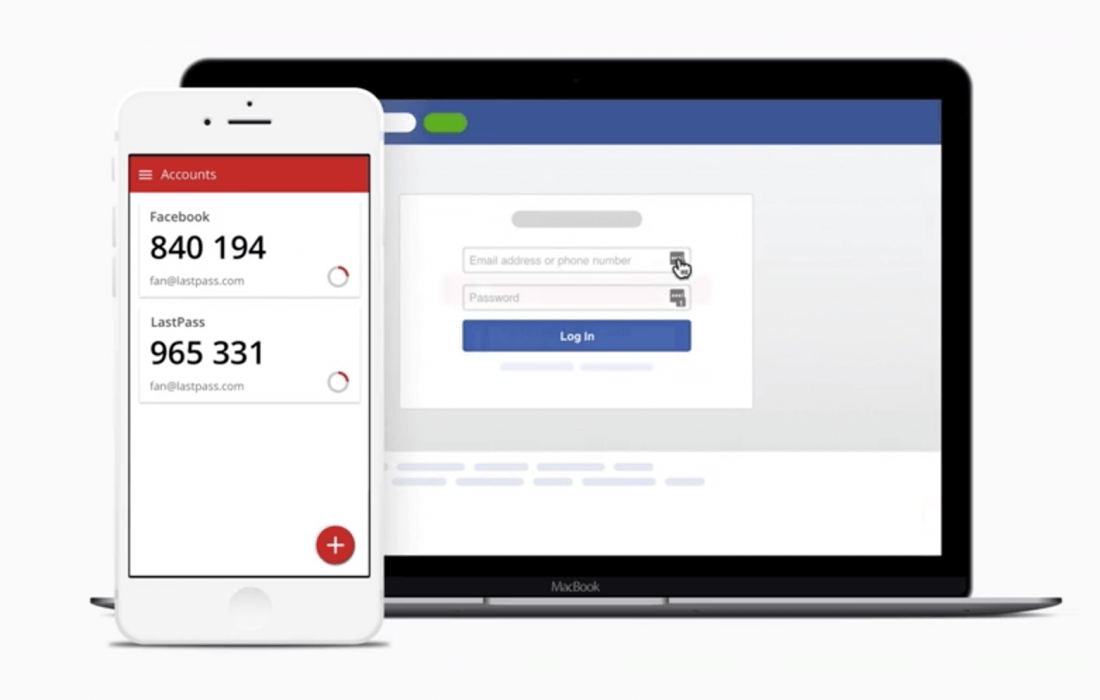
Guide - Two-Factor Authentication: Methods and Myths
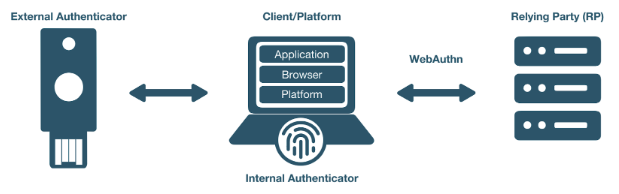
WebAuthn Readiness Checklist
