
Windows, Linux Devices Hijacked In Two-Year Cryptojacking Ca - vulnerability database

Log4Shell Makes Its Appearance in Hacker Chatter: 4 Observat - vulnerability database
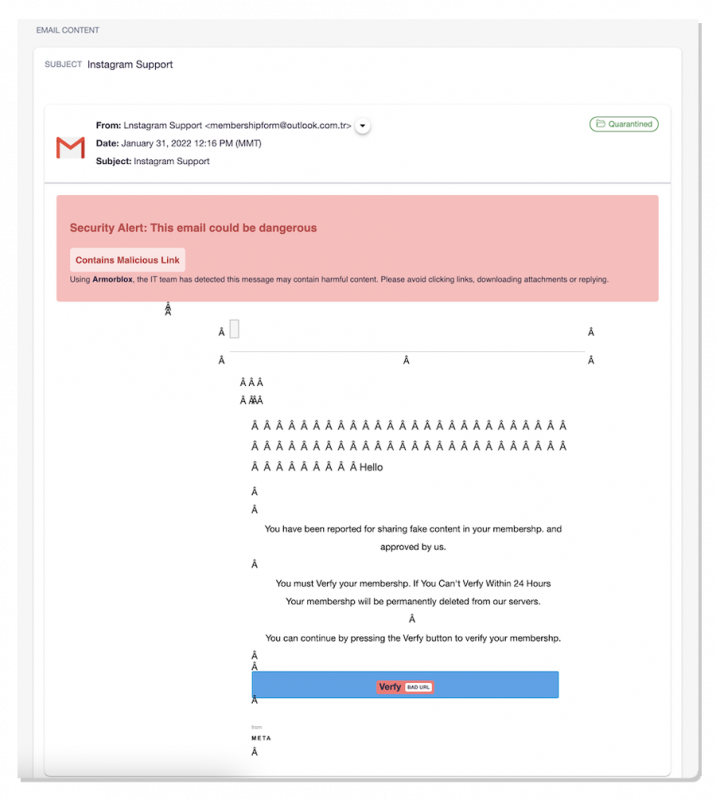
Phony Instagram 'Support Staff' Emails Hit Insurance Company - vulnerability database

Apache Struts Vulnerability (CVE-2017-5638) Exploit Traffic - vulnerability database
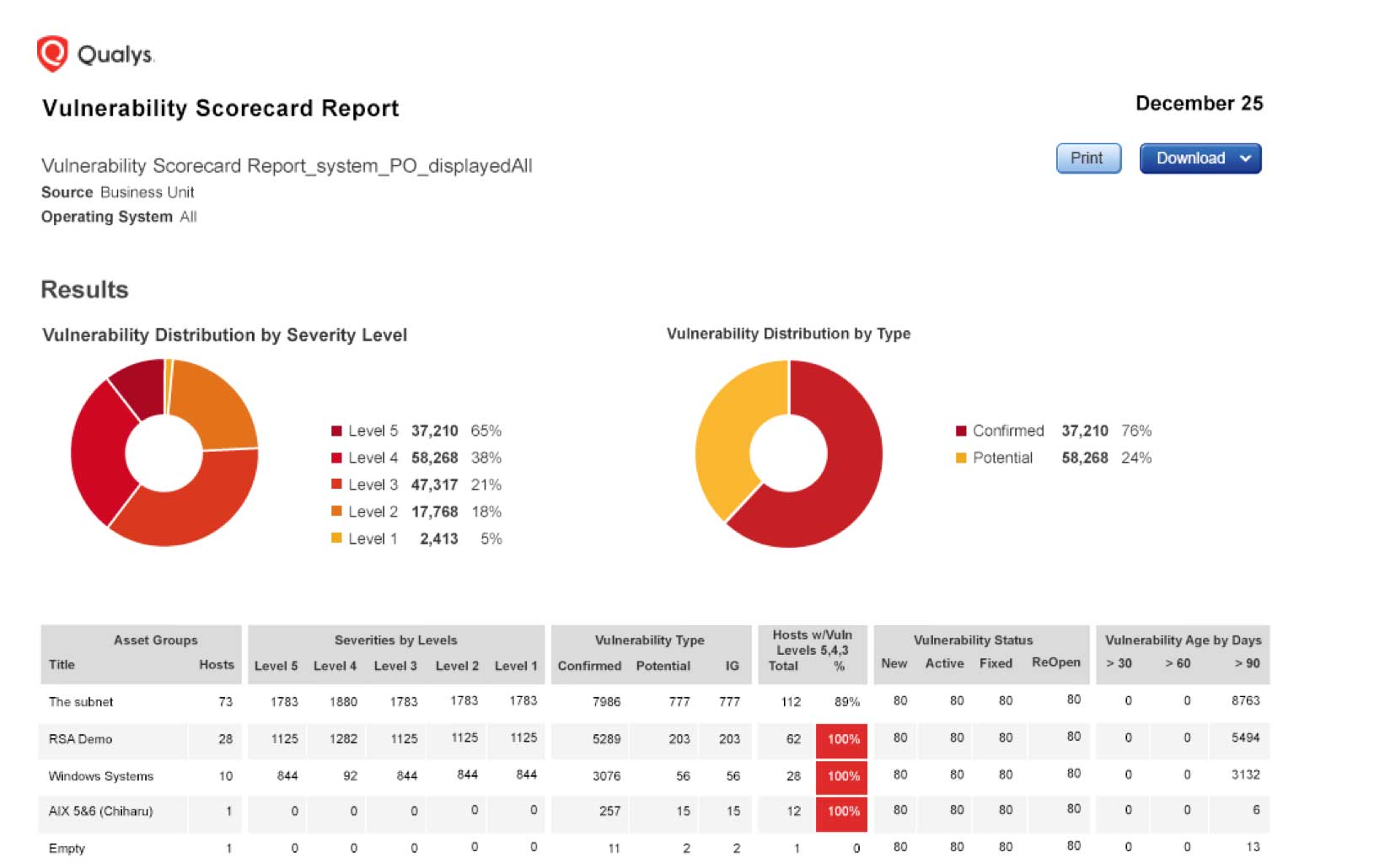
How To Prioritize Vulnerabilities in a Modern IT Environment - vulnerability database

Linux is secure…right? - vulnerability database

Drive-by download campaign targets Chinese websites, experim - vulnerability database

How To Prioritize Vulnerabilities in a Modern IT Environment - vulnerability database

At Tatiana, Food is Memory. It is also magnificent.

APT review: what the world's threat actors got up to in 2019 - blog database
World Turn'd Upside Down: Secret Life of Bloggers Blog Party Post

Using InsightVM to Find Apache Log4j CVE-2021-44228 - vulnerability database

Log4Shell Makes Its Appearance in Hacker Chatter: 4 Observat - vulnerability database
